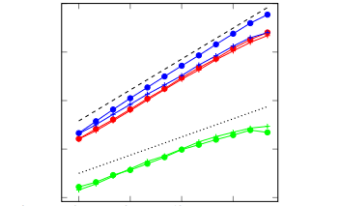
Assuming that Alice commits to an embedding method and the Warden to a detector, we study how much information Alice can communicate at a constant level of statistical detectability over potentially infinitely many uses of the stego channel. When Alice is allowed to allocate her payload across multiple cover objects, we find that certain payload allocation strategies that are informed by a steganography detector exhibit super-square root secure payload (scaling exponent 0.85) for at least tens of thousands of uses of the stego channel. We analyze our experiments with a source model of soft outputs of the detector across images and show how the model determines the scaling of the secure payload.



Historically, two different strategies have been proposed for improving steganographic security by allowing each cover element to be modified by +1 or −1 with unequal probabilities: side-informed steganography and methods that cluster the polarity of neighboring changes. In the first strategy, the sender typically uses the knowledge of quantization errors when developing / processing the cover before embedding. In the latter, embedding on disjoint sub-lattices employs heuristic rules to increase the probability that the polarities of neighboring changes align. In this paper, we propose a method for combining both strategies and experimentally show an improvement in empirical security for several types of side information on two datasets when steganalyzing with rich models as well as convolutional neural networks.

The widespread use of text over online social networks makes it quite suitable for steganography. Conventional text steganography usually transmits the secret data by either slightly modifying the given text or hiding the secret data through synonym replacement. The rapid development of deep neural networks (DNNs) has led automatically generating the steganographic text to become an important and promising topic. This has motivated us to propose a novel generative text steganographic method based on long short-term memory (LSTM) network in this paper. We apply attention mechanism with keywords to the LSTM network to generate the steganographic text. Experiments show that, compared to the related work, the steganographic text generated by the proposed method is of higher semantic quality and more capable of resisting against steganalysis, which has shown the superiority.


The goal of this article is construction of steganalyzers capable of detecting a variety of embedding algorithms and possibly identifying the steganographic method. Since deep learning today can achieve markedly better performance than other machine learning tools, our detectors are deep residual convolutional neural networks. We explore binary classifiers trained as cover versus all stego, multi-class detectors, and bucket detectors in a feature space obtained as a concatenation of features extracted by networks trained on individual stego algorithms. The accuracy of the detector to identify steganography is compared with dedicated detectors trained for a specific embedding algorithm. While the loss of detection accuracy w.r.t. increasing number of steganographic algorithms increases only slightly as long as the embedding schemes are known, the ability of the detector to generalize to previously unseen steganography remains a challenging task.

The number and availability of stegonographic embedding algorithms continues to grow. Many traditional blind steganalysis frameworks require training examples from every embedding algorithm, but collecting, storing and processing representative examples of each algorithm can quickly become untenable. Our motivation for this paper is to create a straight-forward, nondata-intensive framework for blind steganalysis that only requires examples of cover images and a single embedding algorithm for training. Our blind steganalysis framework addresses the case of algorithm mismatch, where a classifier is trained on one algorithm and tested on another, with four spatial embedding algorithms: LSB matching, MiPOD, S-UNIWARD and WOW. We use RAW image data from the BOSSbase database and and data collected from six iPhone devices. Ensemble Classifiers with Spatial Rich Model features are trained on a single embedding algorithm and tested on each of the four algorithms. Classifiers trained on MiPOD, S-UNIWARD and WOW data achieve decent error rates when testing on all four algorithms. Most notably, an Ensemble Classifier with an adjusted decision threshold trained on LSB matching data achieves decent detection results on MiPOD, S-UNIWARD and WOW data.

In this paper, we present a new reference dataset simulating digital evidence for image (photographic) steganography. Steganography detection is a digital image forensic topic that is relatively unknown in practical forensics, although stego app use in the wild is on the rise. This paper introduces the first database consisting of mobile phone photographs and stego images produced from mobile stego apps, including a rich set of side information, offering simulated digital evidence. StegoAppDB, a steganography apps forensics image database, contains over 810,000 innocent and stego images using a minimum of 10 different phone models from 24 distinct devices, with detailed provenanced data comprising a wide range of ISO and exposure settings, EXIF data, message information, embedding rates, etc. We develop a camera app, Cameraw, specifically for data acquisition, with multiple images per scene, saving simultaneously in both DNG and high-quality JPEG formats. Stego images are created from these original images using selected mobile stego apps through a careful process of reverse engineering. StegoAppDB contains cover-stego image pairs including for apps that resize the stego dimensions. We retain the original devices and continue to enlarge the database, and encourage the image forensics community to use StegoAppDB. While designed for steganography, we discuss uses of this publicly available database to other digital image forensic topics.

In this paper, we introduce a new and novel graph-theoretic steganographic approach applicable to online social networking services (SNSs). The proposed approach translates a secret message to be embedded as an undirected graph called messagegraph, the structural information of which is concealed within a new directed graph. The new directed graph is released in a SNS platform by producing a sequence of ordered multiple-user interaction events. To secure communication, we propose to split a specific vertex to multiple copies and insert new vertices and edges to the directed graph. A receiver is able to reconstruct the directed graph from observations. Both the message-graph and the secret message can be orderly retrieved without error. It is probably the first work deeply focusing on the practical design of interaction based steganography using graph-theoretic approach.