
Digital watermarks for texts come in numerous forms. The text itself, but also its appearance, i.e. font, letter spacing or line spacing, can be modified. Here, we present an approach that marks the text itself by introducing changes to the written words. For this, numerous methods are known, such as change from active to passive, modulation of sentence lengths or replacements with synonyms. We use ChatGPT to supplement existing texts with suggestions for synonymous formulations. We also look at evaluating the transparency of the marked texts with the help of ChatGPT.
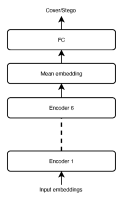
In batch steganography, the sender communicates a secret message by hiding it in a bag of cover objects. The adversary performs the so-called pooled steganalysis in that she inspects the entire bag to detect the presence of secrets. This is typically realized by using a detector trained to detect secrets within a single object, applying it to all objects in the bag, and feeding the detector outputs to a pooling function to obtain the final detection statistic. This paper deals with the problem of building the pooler while keeping in mind that the Warden will need to be able to detect steganography in variable size bags carrying variable payload. We propose a flexible machine learning solution to this challenge in the form of a Transformer Encoder Pooler, which is easily trained to be agnostic to the bag size and payload and offers a better detection accuracy than previously proposed poolers.

Multimedia forensics is an important field addressing the increasing misuse of digital content, such as deepfakes and face-swapping technologies. This paper focuses on detecting face swapping. Our goal is not to decide whether face swapping has occurred. We assume that we execute a forensic investigation in which it needs to be learned which photo of a person’s face has been used for the face swap. We take a number of potential source face photographs and compare their behavior when reproducing the face swap. We show that the photo used for the face swap can be identified even after lossy compression and scaling.
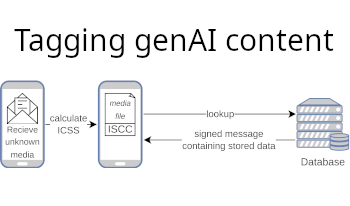
We introduce an initial framework for content traceability in AI-generated media, aligning with the objectives of the EU AI Act. The rapid advancements in generative AI (genAI) necessitate the development of reliable mechanisms for identifying and tracking AI-generated content to ensure transparency, trust and regulatory compliance. To address these challenges, we propose a conceptual infrastructure that facilitates media content registration for AI companies, artists and institutions. It enables provenance tracking and content authentication. Importantly, the proposed system is applicable not only to AI-generated content but also to non-AI-generated media. This dual functionality enhances trust beyond the requirements set forth in the EU AI Act by ensuring the identification of both authentic and synthetic content. The framework incorporates robust hashing techniques, digital signatures, and a database to mitigate the spread of media with uncertain provenance while adhering to regulatory guidelines. A key component of this approach is the adoption of the ISO-standardized International Standard Content Code (ISCC) as a robust hashing method. The ISCC’s decentralized architecture allows for independent implementation without legal constraints, and its adaptability ensures compatibility across various content formats. However, maintaining the flexibility to update hashing algorithms remains essential to address evolving technological advancements and adversarial manipulations.
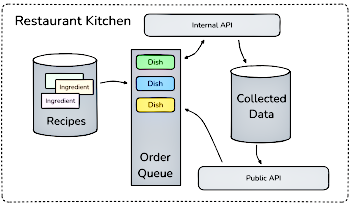
Social media, online forums, darknet marketplaces, and various other digital platforms are increasingly used or targeted by cybercrime. Therefore, open source intelligence (OSINT) has become an important aspect in digital forensics and cybercrime investigations: leveraging publicly available data on the Internet provides new information and offers insights into criminal behavior, patterns, and relationships. Many different tools and services exist to collect and extract data from websites for digital forensic investigations. These are often expensive and prone to errors when target websites change their structure or content. In this paper we present MAMPF, a media acquisition and multi-processing framework for OSINT tasks. The framework is able to collect and extract data from various websites with easy extensibility and maintenance in mind. We show that our framework makes a self-hosted approach to efficient OSINT possible where a centralized core component is utilized in such a way that nodes performing crawling / scraping tasks no not require any maintenance at all. To describe our approach we use the analogy of a restaurant with chefs that prepare dishes following specific recipes.

Reverse Image Search engines play a critical role in Open Source Intelligence (OSINT) and media forensics. They help uncover the origins of images, restoring original contexts and verifying authenticity. This capability is essential for distinguishing benign images from manipulated content. However, the robustness of these search engines is increasingly challenged by the application of post-processing operations and advancements in generative AI, which can produce highly realistic synthetic images. This paper analyzes the robustness of current reverse image search engines and highlights several shortcomings, emphasizing the need for enhanced resilience against AI-generated content to maintain their effectiveness in OSINT and media forensics.