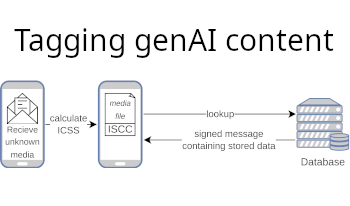
We introduce an initial framework for content traceability in AI-generated media, aligning with the objectives of the EU AI Act. The rapid advancements in generative AI (genAI) necessitate the development of reliable mechanisms for identifying and tracking AI-generated content to ensure transparency, trust and regulatory compliance. To address these challenges, we propose a conceptual infrastructure that facilitates media content registration for AI companies, artists and institutions. It enables provenance tracking and content authentication. Importantly, the proposed system is applicable not only to AI-generated content but also to non-AI-generated media. This dual functionality enhances trust beyond the requirements set forth in the EU AI Act by ensuring the identification of both authentic and synthetic content. The framework incorporates robust hashing techniques, digital signatures, and a database to mitigate the spread of media with uncertain provenance while adhering to regulatory guidelines. A key component of this approach is the adoption of the ISO-standardized International Standard Content Code (ISCC) as a robust hashing method. The ISCC’s decentralized architecture allows for independent implementation without legal constraints, and its adaptability ensures compatibility across various content formats. However, maintaining the flexibility to update hashing algorithms remains essential to address evolving technological advancements and adversarial manipulations.
The ease of capturing, manipulating, distributing, and consuming digital media (e.g., images, audio, video, graphics, and text) has enabled new applications and brought a number of important security challenges to the forefront. These challenges have prompted significant research and development in the areas of digital watermarking, steganography, data hiding, forensics, deepfakes, media identification, biometrics, and encryption to protect owners’ rights, establish provenance and veracity of content, and to preserve privacy. Research results in these areas has been translated into new paradigms and applications for monetizing media while maintaining ownership rights, and new biometric and forensic identification techniques for novel methods for ensuring privacy. The Media Watermarking, Security, and Forensics Conference is a premier destination for disseminating high-quality, cutting-edge research in these areas. The conference provides an excellent venue for researchers and practitioners to present their innovative work as well as to keep abreast of the latest developments in watermarking, security, and forensics. Early results and fresh ideas are particularly encouraged and supported by the conference review format: only a structured abstract describing the work in progress and preliminary results is initially required and the full paper is requested just before the conference. A strong focus on how research results are applied by industry, in practice, also gives the conference its unique flavor.

In this work, we present an efficient multi-bit deep image watermarking method that is cover-agnostic yet also robust to geometric distortions such as translation and scaling as well as other distortions such as JPEG compression and noise. Our design consists of a light-weight watermark encoder jointly trained with a deep neural network based decoder. Such a design allows us to retain the efficiency of the encoder while fully utilizing the power of a deep neural network. Moreover, the watermark encoder is independent of the image content, allowing users to pre-generate the watermarks for further efficiency. To offer robustness towards geometric transformations, we introduced a learned model for predicting the scale and offset of the watermarked images. Moreover, our watermark encoder is independent of the image content, making the generated watermarks universally applicable to different cover images. Experiments show that our method outperforms comparably efficient watermarking methods by a large margin.

The ease of capturing, manipulating, distributing, and consuming digital media (e.g. images, audio, video, graphics, and text) has motivated new applications and raised a number of important security challenges to the forefront. These applications and challenges have prompted significant research and development activities in the areas of digital watermarking, steganography, data hiding, forensics, media identification, and encryption to protect the authenticity, security, and ownership of media objects. Research results in these areas have translated into new paradigms and applications to monetize media objects without violating their ownership rights. The Media Watermarking, Security, and Forensics conference is a premier destination for disseminating high-quality, cutting-edge research in these areas. The conference provides an excellent venue for researchers and practitioners to present their innovative work as well as to keep abreast with the latest developments in watermarking, security, and forensics. The technical program will also be complemented by keynote talks, panel sessions, and short demos involving both academic and industrial researchers/ practitioners. This strong focus on how research results are applied in practice by the industry gives the conference its unique flavor.

In this paper, we reveal the impact of the fixed synchronization pattern on the halftone image under DBS processing; and an improved watermarking method is proposed to avoid this impact, which is extended from a previously developed DBS based watermarking method. The watermark and synchronization pattern is to be embedded into the appropriate region of the host image adaptively; and excellent image quality and decent watermark capacity is provided. The method has good resistance to a printing and scanning attack while only size of the watermark and host image is required additionally in the watermark detection. Experimental results are presented for some special host images, including a sketch and a round logo to prove the flexibility of the method.