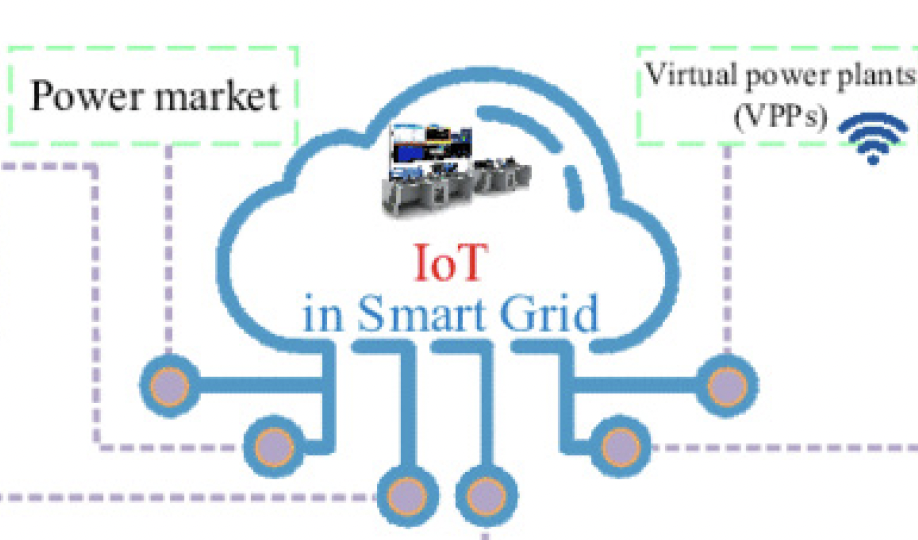
Critical infrastructure is the backbone of modern societies, and protecting this infrastructure is essential to ensure the stability of societies and economies. The electricity sector is one of the most critical infrastructures, and any disruption can have significant consequences. The threat landscape in this sector is constantly evolving. With the increasing sophistication of cyber-attacks and other threats, it has become essential to use innovative technologies to identify and mitigate them. Open Source Intelligence (OSINT) technologies have emerged and offer valuable tools for identifying and mitigating these threats. This article presents an in-depth overview of OSINT technologies and their applications in the protection of critical infrastructure, with an emphasis on the electricity sector. It discusses the vulnerabilities of the electricity sector, the types of OSINT technologies, and the benefits they provide. Case studies of successful applications of OSINT technologies in the electricity sector are presented to illustrate their effectiveness. This article also examines organizations challenges in implementing OSINT technologies, including technological, legal, and financial challenges. Finally, the article concludes by offering recommendations for successfully implementing OSINT technologies to protect critical infrastructure, particularly in the electricity sector. The insights offered in this article will be helpful for policymakers, security professionals, and anyone interested in protecting critical infrastructure.
Open-source technologies (OSINT) and Social Media Intelligence (SOCMINT) are becoming increasingly popular with investigative and government agencies, intelligence services, media companies, and corporations - but also for cybercriminals in email phishing. The amount of public and private data available is rising rapidly. OSINT and SOCMINT technologies use sophisticated techniques and special tools to analyze the continually growing sources of information efficiently. This work aims to find descriptive information using the OSINT tools available online. The target will be achieved with the help of dummy accounts that would help understand the tools and evaluate further different tools. Also, find out what tools are commonly used and what improvements can be made to make them more descriptive for analysts.

Nowadays, almost everyone owns a device capable of photography. More and more photos are taken and distributed through the Internet. In the times of analogue photography, pictures were considered to be legally accepted evidence, but today, due to the multitude of possibilities to manipulate digital pictures, this is not necessarily the case. Metadata can provide information about the origin of the image. The prerequisite for this is that they have not been altered. This work shows possibilities how metadata can be extracted and verified. The additional meta information of an image and its standards are of central importance. We introduce a method of comparing metadata with the visual image content. For this purpose, we apply machine learning for automatically classifying information from the image. Finally, an exemplary verification of the metadata by means of the weather is carried out to provide a practical example of how the presented approach works. Based on this example and on the presented concept, verifiers for metadata that verify several aspects can be created in the future. These verifiers can help to detect forged metadata in a forensic investigation.