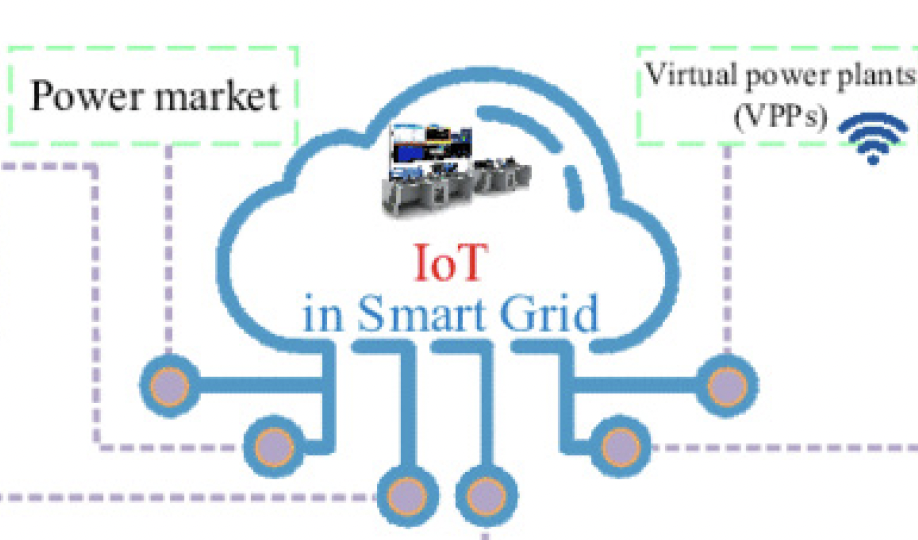
Critical infrastructure is the backbone of modern societies, and protecting this infrastructure is essential to ensure the stability of societies and economies. The electricity sector is one of the most critical infrastructures, and any disruption can have significant consequences. The threat landscape in this sector is constantly evolving. With the increasing sophistication of cyber-attacks and other threats, it has become essential to use innovative technologies to identify and mitigate them. Open Source Intelligence (OSINT) technologies have emerged and offer valuable tools for identifying and mitigating these threats. This article presents an in-depth overview of OSINT technologies and their applications in the protection of critical infrastructure, with an emphasis on the electricity sector. It discusses the vulnerabilities of the electricity sector, the types of OSINT technologies, and the benefits they provide. Case studies of successful applications of OSINT technologies in the electricity sector are presented to illustrate their effectiveness. This article also examines organizations challenges in implementing OSINT technologies, including technological, legal, and financial challenges. Finally, the article concludes by offering recommendations for successfully implementing OSINT technologies to protect critical infrastructure, particularly in the electricity sector. The insights offered in this article will be helpful for policymakers, security professionals, and anyone interested in protecting critical infrastructure.
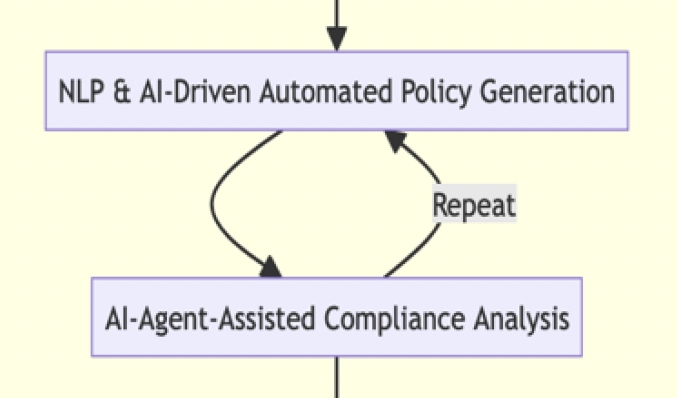
This paper introduces AI-based Cybersecurity Management Consulting (AI-CMC) as a disruptive technology to address the growing complexity of cybersecurity threats. AI-CMC combines advanced AI techniques with cybersecurity management, offering proactive and adaptive strategies through machine learning, natural language processing, and big data analytics. It enables real-time threat detection, predictive analytics, and intelligent decision-making. The paper explores AI-CMC's data-driven approach, learning models, and collaborative framework, demonstrating its potential to revolutionize cyber-security. It examines AI-CMC's benefits, challenges, and ethical considerations, emphasizing transparency and bias mitigation. A roadmap for transitioning to AI-CMC and its implications for industry standards, policies, and global strategies are discussed. Despite potential limitations and vulnerabilities, AI-CMC offers transformative solutions for enhancing threat resilience and safeguarding digital assets, calling for collaborative efforts and responsible use for a secure digital future.
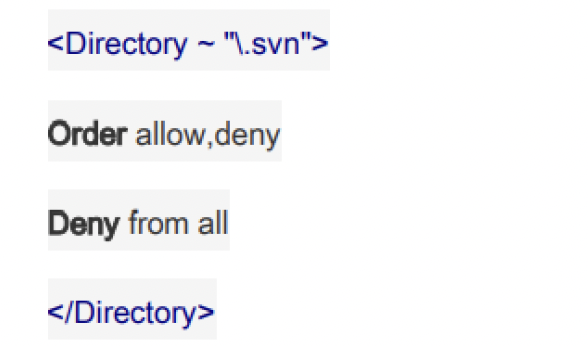
In today's cybersecurity landscape, protecting information systems is crucial due to the rising threat of cyber-attacks. This research focuses on vulnerability management using open-source tools for domain and subdomain enumeration, vulnerability scanning, and remediation. Open-source software offers cost-effective and collaborative security solutions. Domain and subdomain enumeration tools play a vital role in mapping an organization's attack surface, providing insight into security posture. The analysis of vulnerability scanning tools highlights their effectiveness in identifying critical flaws in web applications and databases. Vulnerability remediation through patching, hardening, and exposure management processes closes security gaps. The research provides an empirical insight into using open-source tools for vulnerability management, listing their benefits and limitations empowering organizations to enhance their security posture. Recommendations for integrating these tools into existing security frameworks help combat cyber threats and protect valuable assets.